Friday, April 13, 2012
Hacking with Anti-Android Toolkit | Full Tutorial
Do you like this story?
Here is tut for android users like, i am a andro user :)!
Features:
Scan - This will scan the selected target for open ports and vulnerabilities, also allowing the user to select a specific scanning script for a more advanced/targeted scan.
Spy - This will 'sniff' images transferred to/from the selected device and display them on your phone in a nice gallery layout. If you choose a network subnet/range as target, then all images transferred on that network - for all connected devices - will be shown. Another feature of the Spy plugin is to sniff URLs (web sites) and non-secured (ie, not HTTPS) username/passwords logins, shown on the bottom drawer.
D.O.S - This will cause a Denial Of Service (D.O.S) for the selected target, ie. it will deny them any further access to the internet until you exit the attack.
Replace images - This will replace all images transferred to/from the target with an Anti logo, thus preventing from attacked used seeing any images on their browsers while the browse the Internet, except for a nice looking Anti logo...
M.I.T.M - The Man In The Middle attack (M.I.T.M) is an advanced attack used mainly in combination with other attack. It allows invoking specific filters to manipulate the network data. Users can also add their own mitm filters to create more mitm attacks.
Attack - This will initiate a vulnerability attack using our Cloud service against a specific target. Once executed successfully, it will allow the attack to control the device remotely from your phone.
Report - This will generate a vulnerability report with findings, recommendations and tips on how to fix found vulnerabilities or bad practices used.
Features:
Scan - This will scan the selected target for open ports and vulnerabilities, also allowing the user to select a specific scanning script for a more advanced/targeted scan.
Spy - This will 'sniff' images transferred to/from the selected device and display them on your phone in a nice gallery layout. If you choose a network subnet/range as target, then all images transferred on that network - for all connected devices - will be shown. Another feature of the Spy plugin is to sniff URLs (web sites) and non-secured (ie, not HTTPS) username/passwords logins, shown on the bottom drawer.
D.O.S - This will cause a Denial Of Service (D.O.S) for the selected target, ie. it will deny them any further access to the internet until you exit the attack.
Replace images - This will replace all images transferred to/from the target with an Anti logo, thus preventing from attacked used seeing any images on their browsers while the browse the Internet, except for a nice looking Anti logo...
M.I.T.M - The Man In The Middle attack (M.I.T.M) is an advanced attack used mainly in combination with other attack. It allows invoking specific filters to manipulate the network data. Users can also add their own mitm filters to create more mitm attacks.
Attack - This will initiate a vulnerability attack using our Cloud service against a specific target. Once executed successfully, it will allow the attack to control the device remotely from your phone.
Report - This will generate a vulnerability report with findings, recommendations and tips on how to fix found vulnerabilities or bad practices used.
lets go! guyz!
Go to http://www.zImperium.com/anti.html and follow the instructions there. You will receive a download link to your email. Open this link from your smartphone and then install the app as instructed. (Make sure that 3rd Party Applications is enabled in Settings->Applications->Unknown Sources.)
iOS users can join the list of upcoming (public) BETA testers in the same page, by clicking on the Apple icon.
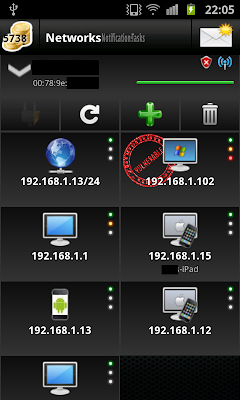
On each run, ANTI will prompt to map the connected network, and when done, it will suggest scanning it for known vulnerabilities and misconfiguration on the targets found. Once a vulnerable target (to remote attacks) is found, it will be marked with red stamp and will appear on the report as a vulnerable device. Displayed in the report is the issue (e.g : MS08-067), how to solve the issue (Windows Update) and how to defend from similar threats in the future (Block port 445 on firewall).
We start by mapping the network - ANTI will scan and detect devices connected to the network. Each device will be displayed with a suitable icon identifying its hardware type and/or the operating system. We can then further scan for vulnerabilities on each of the devices found.
Now that we have our available targets displayed, we can choose any of them to try and penetrate, connect, or sniff network traffic.
The sniffer captures network traffic and displays images, URL’s, user/password combinations, and cookies - all this is collected from the target in real-time, and displayed on ANTI for viewing and examining. We can click on any of the URL’s/cookies to visit the same site our target is visiting.
ANTI also allows us to connect to open ports on the targets, also displaying the opened ports that were found on previous scans.
After playing a bit with the app, I feel comfortable enough to try and penetrate one of my computers, running Windows7 or Mac OS X that are updated only to 1 month prior to this report. I choose the target and click ‘Penetrate CSE’. This plug-in is injecting javascript code using MiTM into target's traffic and redirect traffic to a URL serving Client Side Exploit. Once the target got exploited, ANTI reveals several functions that can be executed over the exploited target: Send screenshot of the current desktop, execute command. The controller functionality is implemented in a very easy-to-use and fun (!) way, allowing both advanced users and home-users to understand the risks of the found vulnerability - while zImperium censored any real possibility to cause real damage to the target, they allow basic information gathering and real life demos such as ejecting the CD-ROM, or grabbing a screenshot (for the assessment’s final report).
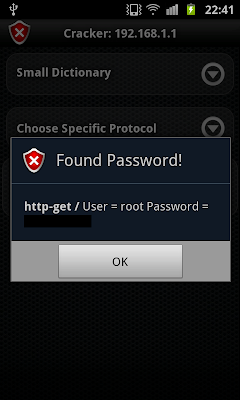
I decided to try the password-cracker on my router. I then realized (the good old hard way) that I better change my password ASAP since it took ANTI less than 30 seconds to crack! Next I executed the cracker on my target running a SQL server and, lo and behold, ANTI didn’t discover the passwords - due to use of high complexity passwords. These results were enough to get me to (finally!) change my router’s password.
There are additional functionalities built into ANTI, such as a unique and fully functional HTTP server that allows publishing files on your device, as well as uploading files to the device, visual traceroute using google-maps, and more.
Once we are done testing, the most important ANTI function is the Report - Everything we have found in the network, vulnerable devices, opened ports, and extra information that will later assist when preparing the assessment report - all is summed up in text and emailed. ANTI3 supports multiple networks so now you can fully use it for your daily penetration tests.
Blog Warning:
HEY VISITORS THIS IS A NOTE FROM ADMIN:
THIS WEBSITE IS BUILD BY ME ONLY FOR EDUCATIONAL PURPOSE I JUST WANT TO PROVIDE CYBER TIPS SO IF U USE THESE INFORMATION TO HARM ANY SUBSTANCE,COMMUNITY OR PERSON AND GOT CAUGHT THEN I AM NOT RESPONSIBLE FOR IT SO MIND MY WORDS HACKING IS A CYBER CRIME DON'T CHEAT OTHERS WITH YOUR POWERS
KNOWLEDGE IS FOR SHARING ASK-SHARE
THIS WEBSITE IS BUILD BY ME ONLY FOR EDUCATIONAL PURPOSE I JUST WANT TO PROVIDE CYBER TIPS SO IF U USE THESE INFORMATION TO HARM ANY SUBSTANCE,COMMUNITY OR PERSON AND GOT CAUGHT THEN I AM NOT RESPONSIBLE FOR IT SO MIND MY WORDS HACKING IS A CYBER CRIME DON'T CHEAT OTHERS WITH YOUR POWERS
KNOWLEDGE IS FOR SHARING ASK-SHARE
FOR MORE INFORMATION MAIL ME:
STSHREYASH50@GMAIL.COM